
When “pretty good” is good enough
PGP stands for “Pretty Good Privacy”. It’s a set of algorithms for encrypting, compressing, and signing data so that a specific person can open and read that data, without a third party being able to also do so. They call it “pretty good” because when you talk about encryption, one of the first things you have to assume is that it’s going to be broken, or is already broken and no one knows. It’s important to know that given enough time, money, and computing power; every encryption can be broken. You also have to realize, There are people in this world who have a much simpler method of breaking encryption and it’s usually called the 5$ wrench attack.

For the most part. Your data is not something that someone is going to spend billions of dollars trying to get at. So long as you’re not in a country that routinely violates human rights, you might also not be susceptible to the 5$ wrench attack. I should note however that it seems people in the United States have been held in prison on contempt of court charges for not giving up decryption keys to encrypted data. It could very well be that you forget passwords to encrypted data and end up languishing in jail. A truly cruel punishment.
More acronyms
So PGP is the standard however it is owned by Symantec and considered proprietary. An open, non proprietary version of this standard is called OpenPGP. OpenPGP is just a concept, a piece of data outlining how OpenPGP works. GPG is actual code that does the things outlined in the OpenPGP standard.
All this lingo and stuff can be confusing so from now on I’ll just be talking about how to use GPG. All you need to take away from that is GPG is a program that let you use the stuff thats outlined in OpenPGP
A word on why
When you talk about securing yourself on the web you have to realize that it’s not just about securing you. Your life might not be at risk because of your views, your government, your ideals, or your beliefs. The thing is there are many people in this world who aren’t so lucky. Whistleblowers, Journalists, political dissidents opposed to fascist regimes all have to worry about whether or not they are going to be found out by someone who may not like what they have to say.
The truth is that using GPG, and encryption in general, normalizes the use of encryption. Imagine if you would, that nobody had locks on their front doors. When walking down the street, you would assume that the only door in the neighborhood with a deadbolt would be hiding something. This is a perfect analogy because it’s also a great response to people who say “Well I have nothing to hide why should I encrypt things”. You’re not hiding anything in your house, why have a lock on the door? Why have a door at all? The answer is that A: You don’t want people wandering in. B: You want to keep bad people out.
The same thing goes for encryption. Your identity is something that you need to protect. Identity theft occurs every day and it has far reaching implications. On top of that. As a society, we need Whistleblowers, Journalists, and yes, sometimes dissidents.
Sending secret messages
We’re going to be talking about Alice, Bob, and Eve. Alice and Bob want to share secret messages and don’t want Eve to be able to read them. Alice and Bob could have something called a Shared secret key that they use to encrypt a message via a Symmetric Encryption algorithm. They both have a copy of the key and therefore can both encrypt and decrypt messages. Eve is out of luck
If you haven’t already, or you’d like an example of this, check out the Encryption Primer to understand a bit more about the basics.
Circling back to GPG
What if Alice and Bob were never in the same room together? As soon as anyone, outside Alice and Bob, put their hands on the secret key, it should be considered compromised and, for all intents and purposes, useless.
This is where Asymmetric encryption comes in. GPG uses something called key-pairs. When Bob wants to get secret information he makes his key pair with an encryption function. That key pair consists of a public key and a private key. Anyone can know the public key. It’s public, and won’t compromise the security of the message. Sometimes it’s helpful to think of the public key as more of a public lock. Anyone can put a message in a box and lock it with that public lock but only Bob can unlock it. Alice also has a key pair. The purpose of these public keys are to both encrypt data and authenticate data. If Alice uses Bob’s public key, she can encrypt any data she likes using it. The only thing that can then decrypt that data, is Bob’s private key. Alice can also sign that encrypted message with her private key and Bob can use Alice’s public key to confirm that it was in fact signed by Alice and therefore likely to contain data that Alice encrypted. Let’s suppose Alice didn’t sign the message she sent to Bob.
1 |
Alice: Bob, Eve is on to us, go dark for a while, I'll let you know when it's less dangerous |
If Alice did sign the message, Bob could in fact decrypt the message but would also know that Alice may not have signed it. Eve doesn’t care what Alice sent Bob in this scenario. In fact she can’t know what the message says (assuming the encryption isn’t broken). She just needs to change what it says and her goals are met.
Asymmetric encryption is often times computationally expensive. In most cases, when someone wants to talk to a specific person, they use the public private key-pair to set up a shared secret key using an algorithm called the Diffie–Hellman key exchange.
In this method, Alice and Bob publicly agree on a shared set of numbers, they then use their private keys and use the public numbers in an algorithm to obtain a “mix” of numbers that they’ll send to one another. Alice and Bob then “mix” the others mixed numbers to be left with a pair of numbers that no one else can know. Eve would need access to either Bob or Alices private numbers in order to arrive at the new secret from any of the numbers that were shared.
It’s a little hard to understand this way, often a good way of explaining this is with colours. The image below shows a representation for this.
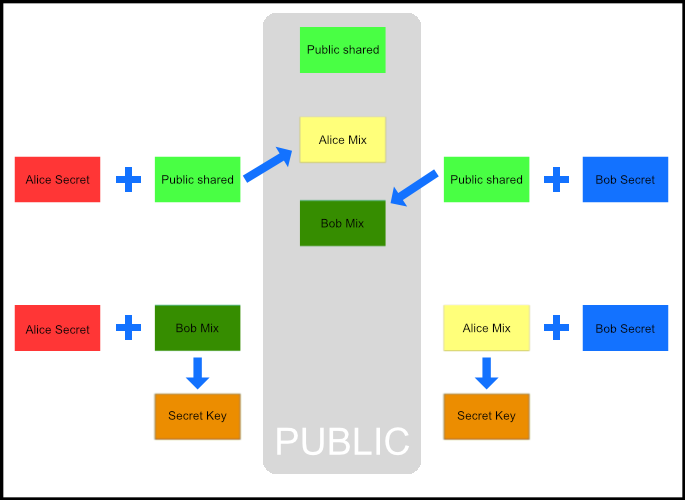
Notice the final colour never goes into the public space. This is the number that would then be used to encrypt messages using a symmetric encryption (similar to our one time pad example). If you’d like to see a video on this, Khan Academy presents a lesson by Brit Cruise and does a good job at demonstrating it.
Putting it all together
Bob and Alice are agents for the super secret Puppy alliance (SSPA). They have never been on the same continent together, let alone met. They’ve both been deployed in the kitty cat capitol city and need to communicate to ensure the survival of puppy dogs in a Feline controlled world. They both know the SSPA’s public key and trust that it belongs to them. Bob, gets a message from Alice that is signed with Alice’s Public key. He can not be sure that the message is in fact from Alice because Eve could have easily made a Public and Private key and called herself Alice. However, the message also contained a signature on Alice’s public key signed by the SSPA. Because Bob trusts the SSPA he can believe that this key in fact does belong to Alice as Eve would have no way of signing the public key with SSPA’s private key.
Using GPG Bob and Alice set up a shared secret and then can communicate in private while Eve is left on the outside not being able to read any of their messages. Puppies will rise again.
All of this just dips our toes into Cryptography, There is much more to know. There are several different parts of a crypto system and each have very specific uses. In later posts I will try to outline how to make some solid keys, the different
useful features of other systems, and more info on why it’s a good idea to not make crypto yourself and instead rely on the genius of others. Until then, try to come up with an explanation of forward secrecy. Think about how
you could change your key every message, Think about what would happen if you received a message out of order in that scenario. How would you protect earlier messages from being decrypted if your key was leaked?
As always, let me know if you have any questions or something you’d like me to add.